17 Mar 2021
Blogs
Patching for HAFNIUM is just half of the story
UPDATE 2021-03-17
Altered the diagram with respect to new guidance from Microsoft [6]
On the 2nd of March, a posting by The Department of Homeland Security (U.S.) didn’t mince its words and placed an Emergency Directive to perform a thorough check of any Microsoft Exchange servers at your control [1]. This article served a guide for “agencies that have the expertise” to “forensically triage artefacts”.
Note that the 2nd of March was two weeks ago now – since then there have been a number of tools that have been made available to enable the task of identifying, checking, mitigating, patching, and cleaning of your servers and systems [2][3][4].
These tools were created to help caretakers of Microsoft Exchange Servers that are deemed vulnerable to quickly AND efficiently purge – to the best effort possible – any compromise(s) of the servers.
The lesson here is that there has been (and this continues to grow) a huge amount of effort in making sure that caretakers go beyond the simple sole act of patching.
Currently there are activities from third-parties to help notify those caretakers of Exchange Servers should their systems appear flagged as being vulnerable. More often than not, the response may be is “It’s OK, we have just patched!”. Whilst this in itself is good, in the light of the fact that these vulnerabilities were 0-day, and the patch came after exploit activities were detected, ALL instances of the Exchange Server needs to be checked if any compromise(s) have happened – due to the fact that persistent mechanisms, such as a webshell(s), may have been already installed.
Indicators of Compromise are being gathered on a daily basis [5], and the tools are being revamped so it also means that each time there is an update to the tools made available, it may also be wise to check if the newest version picks anything up!
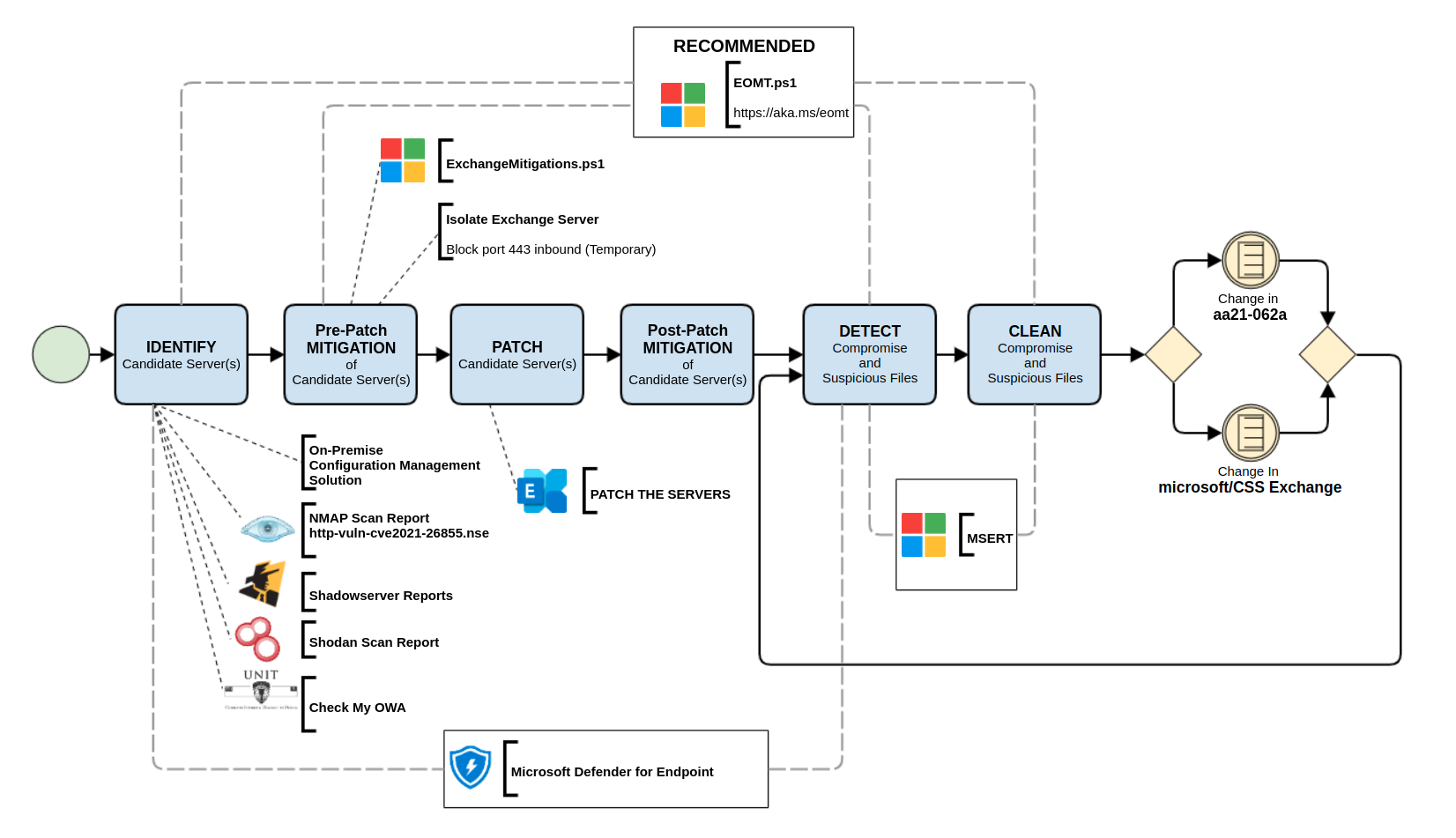
A diagram (see below) has been created by our team, which should assist Microsoft Exchange server caretakers to check and see where in their task-flow they are at.
Let it be noted there is no real hard-stop listed on this diagram. Until there are no more indicators being published and the tool(s) have stopped being updated, we recommend referring to it. Additionally, there are bound to be more useful tool(s) made available after the publication of this article – so do stay vigilant!
Good luck, stay informed and stay safe.
AUSCERT Team
References
[1] https://cyber.dhs.gov/ed/21-02/
[2] https://github.com/microsoft/CSS-Exchange/tree/main/Security
[3] https://github.com/ANSSI-FR/DFIR-O365RC
[4] https://checkmyowa.unit221b.com/
[5] https://us-cert.cisa.gov/ncas/alerts/aa21-062a
Resource noted in Diagram
NMAP Scan Report – http-vuln-cve2021-26855.nse
https://github.com/microsoft/CSS-Exchange/tree/main/Security#http-vuln-cve2021-26855nse
Shadowserver Reports
March 11 ’21 https://www.shadowserver.org/news/shadowserver-special-reports-exchange-scanning/
March 12 ’21 https://www.shadowserver.org/news/shadowserver-special-reports-exchange-scanning-2/
March 15 ’21 https://www.shadowserver.org/news/shadowserver-special-reports-exchange-scanning-3/
March 15 ’21 https://www.shadowserver.org/news/shadowserver-special-reports-exchange-scanning-4/
Microsoft Defender for Endpoint
https://www.microsoft.com/en-au/microsoft-365/security/endpoint-defender
Check My OWA
https://checkmyowa.unit221b.com/
ExchangeMitigations.ps1
https://github.com/microsoft/CSS-Exchange/tree/main/Security#exchangemitigationsps1
PATCH THE SERVERS
microsoft/CSS-Exchange
https://github.com/microsoft/CSS-Exchange/tree/main/Security
aa21-062a
https://us-cert.cisa.gov/ncas/alerts/aa21-062a





